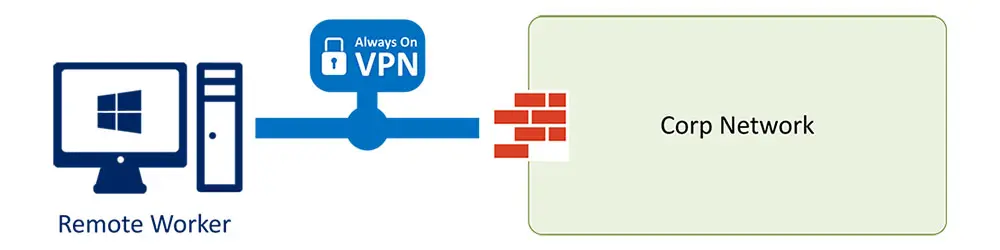
Always On VPN is an interesting technology which makes access to company resources from outside of organization network absolutely seamless for domain joined devices. It doesn’t matter if the client is Active Directory domain joined, Azure Active Directory joined or a Hybrid joined device.
With AAD Joined devices and Windows Hello for Business (key or certificate trust) it is even possible to have On-premises Single-sign On.
What does Always On VPN mean?
The main difference between a common VPN and Always On VPN is basically, that this VPN automatically connects in the background, when the User is outside of the corporate network and has Internet access.
There are two types of tunnels:
- User Tunnel
- Device Tunnel
Each of them has it’s advantages and you can even run both of them together. So let’s compare them a little:
| Device Tunnel | User Tunnel | |
|---|---|---|
| Requirements |
|
|
| Advantages |
|
|
| Disadvantages |
|
|
Network Overview – The Big Picture
This overview shows a purely Azure AD joined and Intune managed Windows 10 device using Always On VPN. To get that work the following components are involved:
- The basis: Active Directory with User Sync to Azure AD
- The Certification part: Enterprise CA with CRL Publishing Webserver and NDES (with Intune Connector installed)
- Azure App Proxy as a Reverse Proxy for the CRL Webserver and NDES Server
- Network Policy Sever (NPS)
- VPN Server: Remote Access Server (RAS)
- Microsoft Intune for Certificate Profiles Deployment
In this deployment on the Enterprise CA a User Certificate Template will be created and enrolled with NDES / Intune. In the perimeter network a Remote Access Server (RAS) will be deployed, with one interface on the external perimeter and the other on the internal permieter. Dependig on your network there is maybe just one firewall.
On the internal perimeter interface we have also the VPN IP address range for the clients connecting to that VPN.
For IKEv2 we need to open the UDP ports 500 and 4500 on our external perimeter firewall and NAT the traffic to the RAS. The RAS then communicates with the NPS on UDP ports 1812-1813 and optional 1645-1646 to authenticate the user.
For the VPN Client IPs we now have to open the necessary ports to the services which should be available to the clients, e.g. DNS or File Server access. You can also make traffic filters directly in Intune on the VPN Configuration profile.
I described this client configuration part (User Certificate and VPN Client Configuration) in a little article series. Here you can directly jump to Part 1.