If you have configured SharePoint to authenticate through ADFS you need to export the ADFS Token-signing Certificate and set that on SharePoint side.
This Token-signing certificate renews on an annual basis and as soon it’s replaced on ADFS side it must be replaced on SharePoint side too.
Otherwise you can get a not very meaningful runtime error on IIS after ADFS sign-in.
If you modify customErrors to <customErrors mode=”RemoteOnly” /> the full error message appears, indicating a certificate issue:
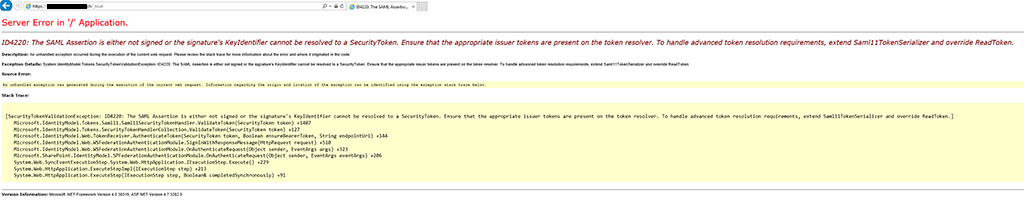
Full Error message:
Server Error in ‘/’ Application.
ID4220 The SAML Assertion is either not signed or the signature’s KeyIdentifier cannot be resolved to a SecurityToken. Ensure that the appropriate issuer tokens are present on the token resolver. To handle advanced token resolution requirements, extend Saml11TokenSerializer and override ReadToken.
Description An unhandled exception occurred during the execution of the current web request. Please review the stack trace for more information about the error and where it originated in the code.Exception Details System.IdentityModel.Tokens.SecurityTokenValidationException ID4220 The SAML Assertion is either not signed or the signature’s KeyIdentifier cannot be resolved to a SecurityToken. Ensure that the appropriate issuer tokens are present on the token resolver. To handle advanced token resolution requirements, extend Saml11TokenSerializer and override ReadToken.
Source Error
An unhandled exception was generated during the execution of the current web request. Information regarding the origin and location of the exception can be identified using the exception stack trace below.Stack Trace
[SecurityTokenValidationException ID4220 The SAML Assertion is either not signed or the signature’s KeyIdentifier cannot be resolved to a SecurityToken. Ensure that the appropriate issuer tokens are present on the token resolver. To handle advanced token resolution requirements, extend Saml11TokenSerializer and override ReadToken.]
Microsoft.IdentityModel.Tokens.Saml11.Saml11SecurityTokenHandler.ValidateToken(SecurityToken token) +1407
Microsoft.IdentityModel.Tokens.SecurityTokenHandlerCollection.ValidateToken(SecurityToken token) +127
Microsoft.IdentityModel.Web.TokenReceiver.AuthenticateToken(SecurityToken token, Boolean ensureBearerToken, String endpointUri) +144
Microsoft.IdentityModel.Web.WSFederationAuthenticationModule.SignInWithResponseMessage(HttpRequest request) +510
Microsoft.IdentityModel.Web.WSFederationAuthenticationModule.OnAuthenticateRequest(Object sender, EventArgs args) +323
Microsoft.SharePoint.IdentityModel.SPFederationAuthenticationModule.OnAuthenticateRequest(Object sender, EventArgs eventArgs) +206
System.Web.SyncEventExecutionStep.System.Web.HttpApplication.IExecutionStep.Execute() +229
System.Web.HttpApplication.ExecuteStepImpl(IExecutionStep step) +213
System.Web.HttpApplication.ExecuteStep(IExecutionStep step, Boolean& completedSynchronously) +91
Solution
- On the AD FS Snap-In open Service > Certificates
- Go to Token-signing and double click the primary certificate.
- Go to details, select copy to file and save it.
- Copy the Certificate file to your SharePoint Server
- In the SharePoint Management shell type the following commands:
$cert = New-Object System.Security.Cryptography.X509Certificates.X509Certificate2("C:\Install\adfs-token-signing.cer") $sts = Get-SPTrustedIdentityTokenIssuer $sts | Set-SPTrustedIdentityTokenIssuer -ImportTrustCertificate $cert - Add the certificate to the Trusted Root Certification Authorities on SharePoint server


