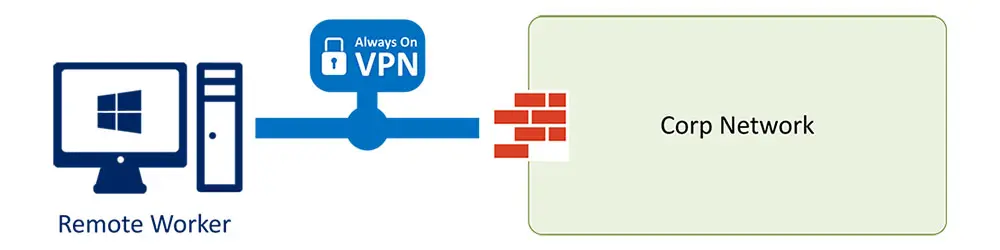
This article series describes the different parts necessary to create an Always On VPN User tunnel based on Enterprise PKI certificates distributed through Intune with a SCEP Certificate Profile.
Prerequisites
- Deploy an Offline Root CA
- Deploy an Enterprise Subordinate CA
- Deploy an Network Device Enrollment Service (NDES) with Intune Connector
- Deploy Routing and Remote Access Server as an Always On VPN Server
- Deploy NPS Server to Support EAP (PEAP / Smart Card or other certificate)
This series covers
- Create the User Authentication Certificate Template for Always On VPN
- Distribute the User Authentication Certificate for Always On VPN with Intune SCEP Certificate Profile
- Create the EAP VPN Connection
- Create the Intune VPN Profile
Create the Intune Always On VPN Profile
Time needed: 15 minutes
This steps are executed on Microsoft Endpoint Manager admin center (https://devicemanagement.microsoft.com/) in Devices, Configuration profiles.
- Create a new Profile and select VPN
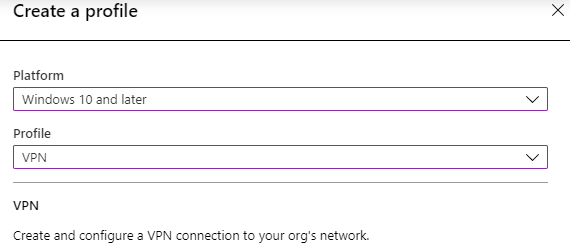
- Basics: Choose a name for your VPN Connection
- Configuration settings: Base VPN
This area contains the name of the VPN connection deployed to the user profile. It also contains one or multiple VPN Server destinations, you have to choose one serve as your default server.
The connection type is IKEv2 and Always On should be turned on. Do also select Remember credentials at each logon and select EAP as Authentication method.
You don’t need to select a certificate here but you have to paste your EAP Configuration from Step 3 into the text area.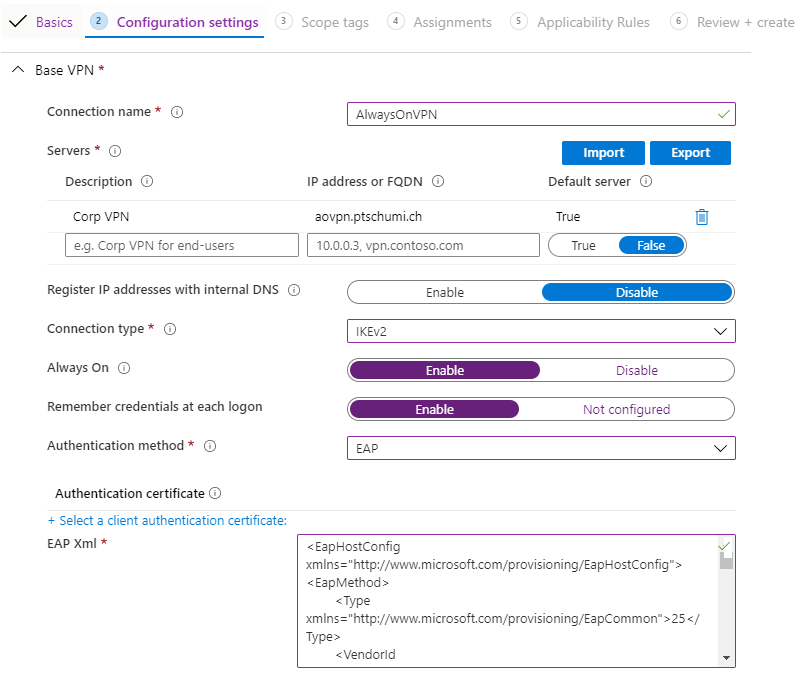
- Configuration settings: App and Traffic Rules
If desired, you can configure Windows Information Protection (WIP) rules or App Rules connected with network traffic rules.
Network traffic Rule types:
Split tunnel = only the traffic meant for the VPN interface (ad determined by the networking stack) goes over the interface. Internet traffic can continue to go over other interfaces.
Force tunnel = all IP traffic must go through the VPN interface only (for this traffic rule).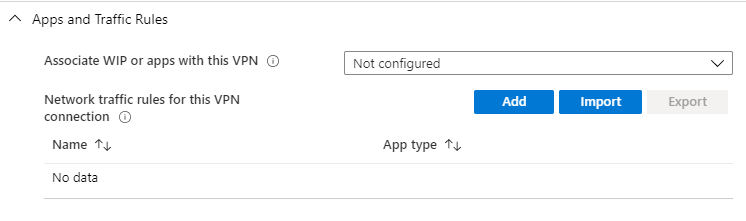
- Configuration settings: Conditional Access
Not part of this configuration.
Enables Device Compliance flow from the client. When enabled, the VPN client will attempt to communicate with AAD to get a certificate to use for authentication. The VPN should be set up to use certificate authentication and the VPN server must trust the server returned by AAD.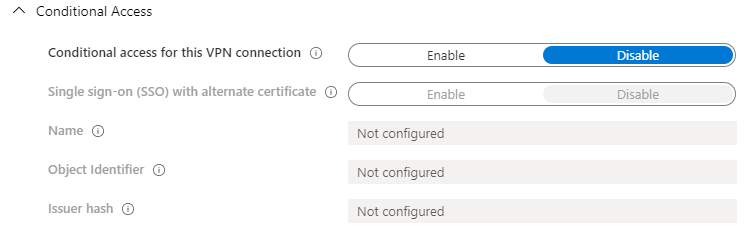
- Configuration settings: DNS suffix search list
Specify DNS suffixes to add to the DNS search list to properly route short names. The first suffix in the list is also used as the primary connection-specific DNS suffix for the VPN interface.
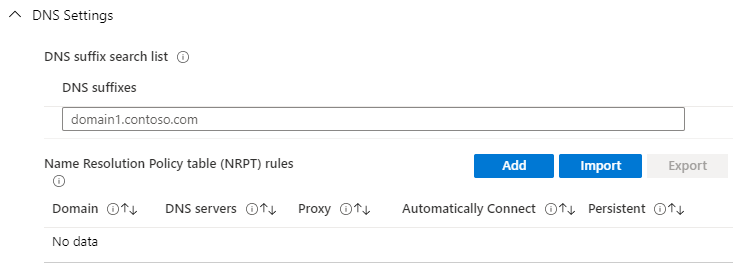
- Configuration settings: Proxy
Add a proxy server configuration if necessary.
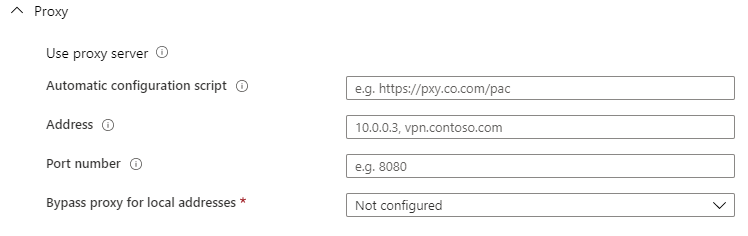
- Configuration settings: Split Tunneling
Enable split tunneling if you only want certain web traffic to use the VPN tunnel. Disable this if you want all traffic to use the VPN tunnel when the VPN connection is active.
If enabled you have to specify the networks / routes which should go through the VPN tunnel.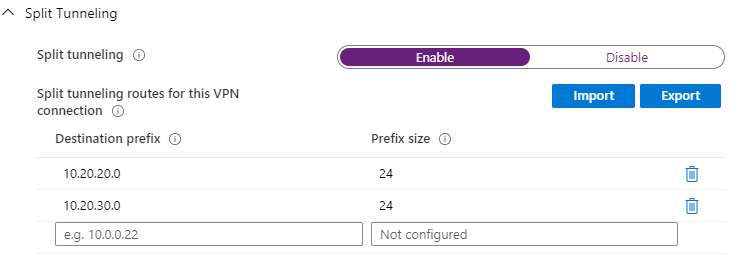
- Configuration settings: Trusted Network Detection
Enter DNS suffixes used to determine if the device is connected to a trusted network. If any of them are reachable by the device, the device will not automatically connect to the VPN, even if there are auto-triggers set.