This article series describes the different parts necessary to create an Always On VPN User tunnel based on Enterprise PKI certificates distributed through Intune with a SCEP Certificate Profile.
Prerequisites
- Deploy an Offline Root CA
- Deploy an Enterprise Subordinate CA
- Deploy an Network Device Enrollment Service (NDES) with Intune Connector
- Deploy Routing and Remote Access Server as an Always On VPN Server
- Deploy NPS Server to Support EAP (PEAP / Smart Card or other certificate)
This series covers
- Create the User Authentication Certificate Template for Always On VPN
- Distribute the User Authentication Certificate for Always On VPN with Intune SCEP Certificate Profile
- Create the EAP VPN Connection
- Create the Intune VPN Profile
Create the User Authentication Certificate Template for Always On VPN
Time needed: 10 minutes
Do not click apply before you have configured all settings!
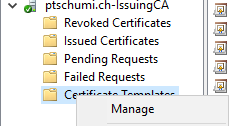
- On the Certification Authority Snap-In right-click Certificate Templates and select Manage
- Duplicate the User Template
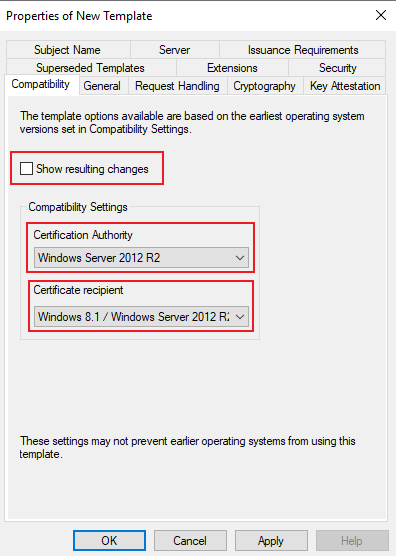
- Configure Compatibility
Disable checkbox Show resulting changes and then select Windows Server 2012 R2 in both Drop Down lists.
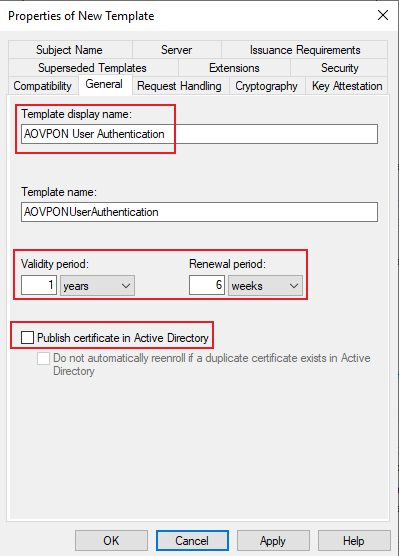
- Configure General
Define the Template display name and the validy you would like, also make sure you disable Publish certificate in Active Directory. Remember the Template name below the display name, you need to assign that name on the NDES.
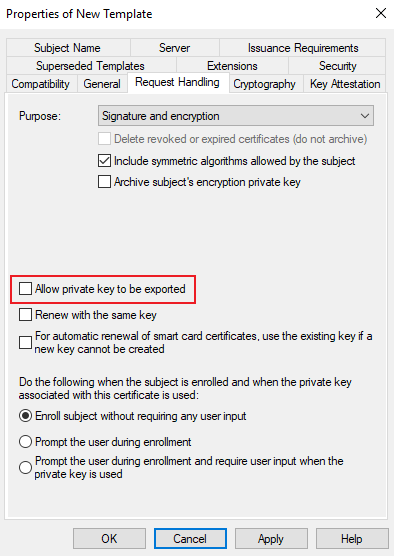
- Configure Request Handling
Unselect Allow private key to be exported
- Configure Cryptography
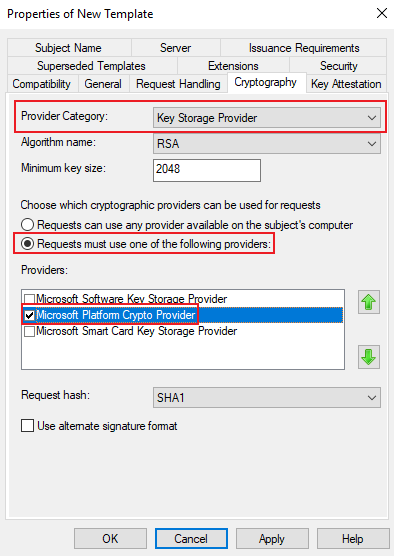
Select Key Storage Provider, make sure Algorithm is RSA and Minimum key size is 2048, select Requests must use one of the following providers and then select Microsoft Platform Crypto Provider.
- Extensions
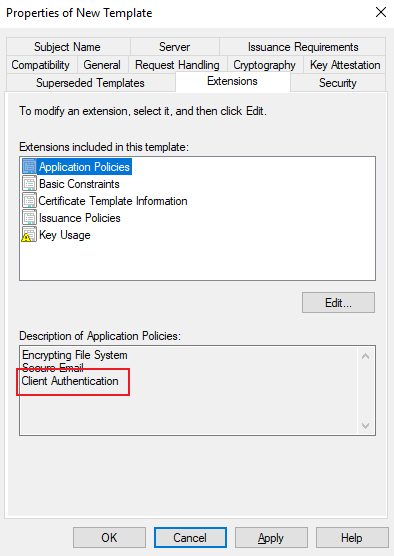
On the extensions tab you don’t need to change anything if you selected the User Template, but verify that Client Authentication is selected.
- Configure Security
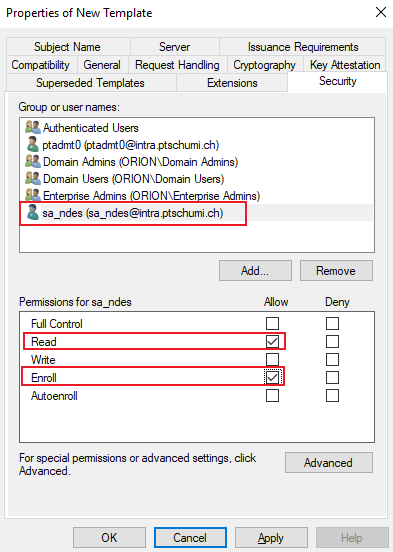
Here you should remove Domain users and make necessary adjustments to your needs. If you your machine is only Azure AD joined and you deploy through Intune / NDES you should add here the NDES Service Account with Read and Enroll permissions. Otherwise, if enrolled to Active directory, add your VPN Users Security Group with Read, Enroll and Autoenroll Permissions.
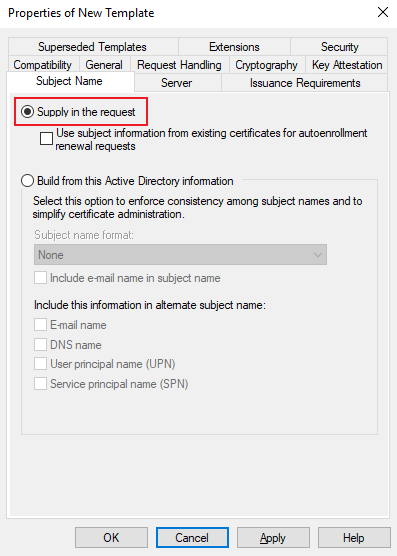
- Configure Subject Name
Here again, for AAD Joined devices, select Supply in the request (this configuration will be done in Intune), for AD Joined devices keep Build from the Active Directory information but clear the checkboxes Include e-mail name in the subject name and E-mail name.